-
|
Hi, I am wondering if anyone has information as to why AWS secrets handling for the
@kaxil - You appear to be the authority on what is there (basing this on one of the latest PRs in AWS systems manager sphere). Thank you for your work on all this. It has made our org happy to have a better method for handling secrets. I am curious though if we had any reason why we have the approach we currently have for this particular error catch. I am somewhat new to Airflow internals and also somewhat new to Python, so I'm hoping, if anything, you can help educate me. |
Beta Was this translation helpful? Give feedback.
Replies: 1 comment 1 reply
-
|
Hi @nsepetys, Glad that you found the secrets backend useful. The main reason we don't raise For example, for Airflow Variables: We do a similar thing for Hashicorp Vault and GoogleCloud Secrets Backend but as they don't raise an error, we just return airflow/airflow/providers/google/cloud/secrets/secret_manager.py Lines 148 to 158 in ffe3bd2 We loop across all the 3 backends (Secrets Backend in the airflow.cfg, Environment Variables and then MetastoreBackend) airflow/airflow/models/connection.py Lines 343 to 354 in a9ac2b0 airflow/airflow/configuration.py Lines 1017 to 1033 in ffe3bd2 We only raise an error when Connection or Variable is not found in all the 3 backends |
Beta Was this translation helpful? Give feedback.
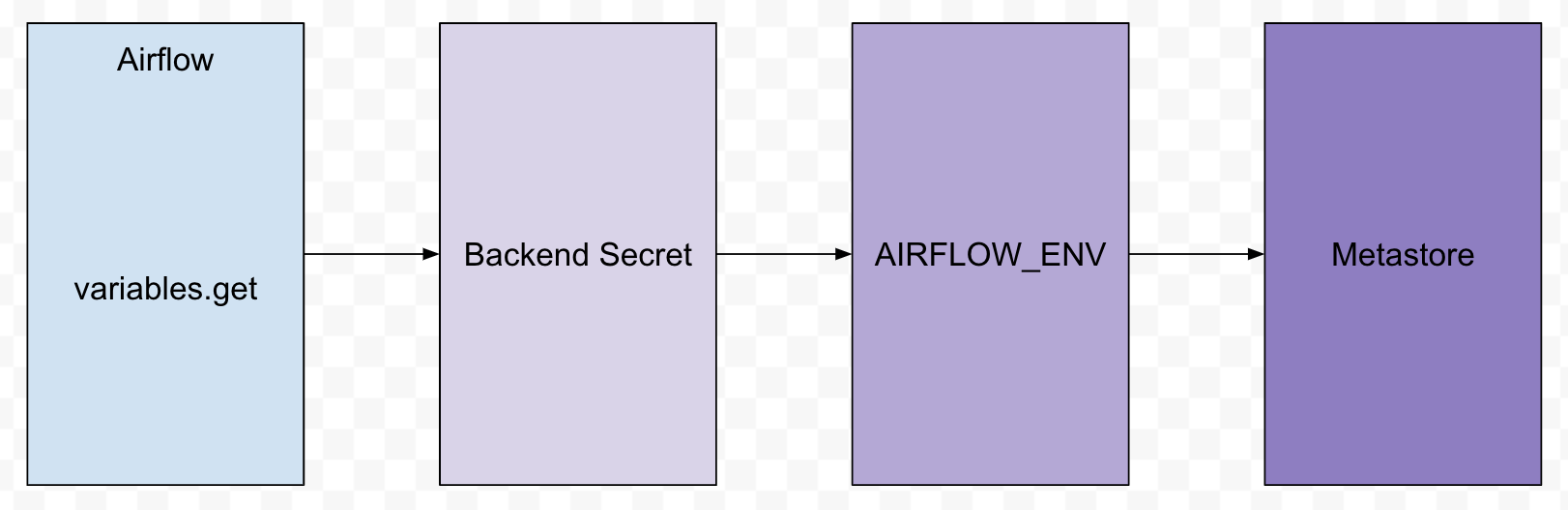
Hi @nsepetys,
Glad that you found the secrets backend useful.
The main reason we don't raise
ParameterNotFoundfor AWS secrets backend (SystemsManagerParameterStoreBackendandSecretsManagerBackend) is so that we can fallback to getting variables or Connections via Environment Variables and then Metadata Database.For example, for Airflow Variables:
We do a similar thing for Hashicorp Vault and GoogleCloud Secrets Backend but as they don't raise an error, we just return
None(e.gairflow/airflow/providers/google/cloud/secrets/secret_manager.py
Lines 148 to 158 in ffe3bd2