-
Notifications
You must be signed in to change notification settings - Fork 0
Home
Welcome to the tugpgp wiki!
The OpenPGP key generated via this application will have a RSA4096 primary key with signing and certification capability, and one subkey for encryption and one for authentication. By default the keys will have 1 year of expiry.
The touch method is Fixed for decryption and signature, for ssh authentication it is of mode On.
We tested it against Yubikey5 and Yubikey 4. It will also disable OTP application in your Yubikey.
We have the 0.1.3a2 DMG for Apple Silicon Macs.
Verify the sha256sum of the files before executing.
7bb5317022a9be9a0096a29b0ce8212657943ee337bf761a74d3838acc8cdcd1 Tugpgp-0.1.3a2.dmg
uv is a modern tool for Python projects. We can use the same to install and run tugpgp on both Mac and Linux.
First install uv itself.
$ curl -LsSf https://astral.sh/uv/install.sh | sh
Make sure it is at least 0.5.18 version.
$ uv --version
uv 0.5.18
Then run the application (you need Internet connection for this).
$ uvx tugpgp
Start the application and keep one (or more) Yubikey ready. We will erase and upload new OpenPGP keys to this Yubikey.

Click next.

Fill up your name and all the email IDs you want in the key, one email address per line. Choose a temporary password (4+ words please).
After you click next, the application will generate the key and show you the next screen.

If you click next, and no Yubikey is attached to the computer, it will show you the error message in red. Connect only the new Yubikey and then click next and then finally click on the "Upload" button.
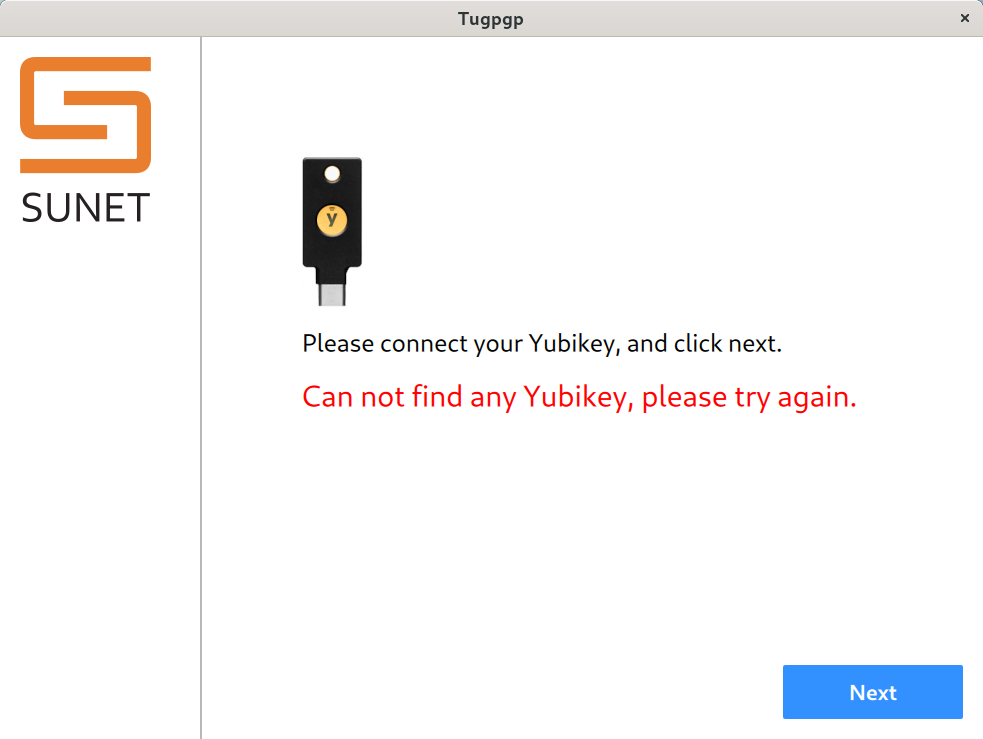

If you click next, it will upload the OpenPGP key to the Yubikey.

The following screen will let you know that the upload was successful.

Next, select a directory to save the Public key. This file is important as you will have to use it in all the places. It will also have a ssh public key with the name starting with ssh-.

Then set the user pin (6+ characters) for daily use of the Yubikey, and then one admin pin (8+ characters).


And then you will reach the final screen, click on "Create backup" and repeat the steps of uploading the OpenPGP key to another Yubikey.

Next, you should import the newly generated key via the command into the tool of your choice.
$ gpg --import ~/5D18C5B6A8A012397201E419ACED1B53D69D4089.pub
You will also your ssh public key in the home directory. Example:
ssh-5D18C5B6A8A012397201E419ACED1B53D69D4089.pub