English 简体中文
The Spire is a high-performance reverse proxy/load balancer. And it could be also used as the ingress controller in the k8s.
We do the performance testing between several popular proxies including NGINX, Envoy, and Caddy. The benchmarks show here.
The test results show that under the same machine configuration (4 cores 8G), in some indicators (requests per second, average response time), the data of Spire is almost the same as the NGINX and Envoy. In terms of request latency, Spire is better than NGINX and Envoy.
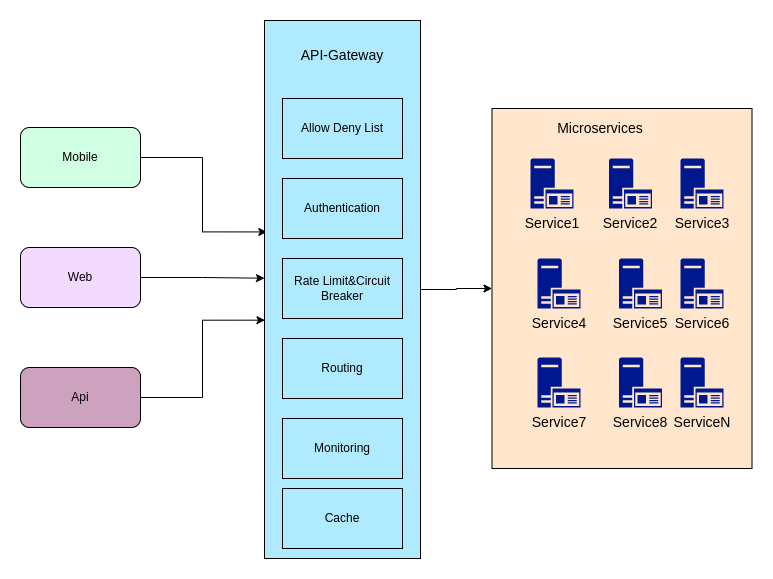
Spire is not only a reverse proxy/load balancer, but also an API gateway. As an API gateway, Spire will cover all basic functions (black and white list/authorization/fuse limit/gray release , blue-green publishing/monitoring/caching/protocol conversion).
Compared with other gateways, Spire has the advantage of covering all the basic services of the API gateway, and has high performance. Second, Spire's dynamic configuration is close to real-time. Every time the configuration is modified, it will take effect within 5 seconds (close to real-time).
The free Ratelimiting plugin for Kong is inaccurate. If we want to achieve more accurate Ratelimiting, we have to buy the enterprise version of Kong.
Envoy does not have built-in ratelimiting. Envoy provides a ratelimiting interface for users to implement by themselves. Currently the most used is this project. The first disadvantage is that the project only supports fixed-window ratelimiting. The disadvantage of the fixed window ratelimiting is that it does not support burst traffic. The second disadvantage is that every time Envoy is requested, it will use grpc to request the ratelimiting cluster. Compared with the built-in current limiting algorithm, this actually adds an additional network hop.
You could change the configuration over the rest API. And the new configuration will have an effect in 5 seconds.
You have to install the rust first.
cd rust-proxy
cargo build --release
You could get the release in the target/release.
Download the release from the website.
static_config:
log_level: info
services:
- listen_port: 8084
service_config:
server_type: http
routes:
- route_id: test_route
matcher:
prefix: /
prefix_rewrite: /
router: http://192.168.0.0:9393
The proxy will listen the 9969 port and forward the traffic to the http://localhost:8888/,http://localhost:9999/.http://localhost:7777/.
static_config:
log_level: info
services:
- listen_port: 8084
service_config:
server_type: http
routes:
- route_id: test_route
matcher:
prefix: /
prefix_rewrite: /
router:
type: file
doc_root: D:\code\github\gitstats\kvrocks
middlewares:
- type: rewrite_headers
expires: 24h
extensions: [js, css, html, png, jpg, gif]
.\target\release\spire.exe -f .\config\app_config_simple.yaml
- http/grpc/websocket/tcp proxy
- IP Allow-and-Deny list
- Authentication(Basic Auth,ApiKey Auth,JWT Auth)
- Rate limiting(Token Bucket,Fixed Window)
- Routing
- Load Balancing(Poll,Random,Weight(Canary Release),Header Based)
- HealthCheck&AnomalyDetection
- Free Https Certificate
- Dynamic Configuration(Rest Api)
- Monitoring(Prometheus)
- Circuit Breaker
- Protocol Translation(Http To Grpc)
- Header Rewrite
- CORS
- Caching