based on:
- if you use more than 1 roadwarrior clients in the same subnet -> they need different "public" transport gateway ips (if possible)
- for example:
- laptop 1 with mac os:
- local network ip AAA.AAA.AAA.101 - default routing over ISP1 gateway YYY.YYY.YYY.1
- laptop 2 with debian linux:
- local network ip BBB.BBB.BBB.102 - default routing over ISP2 gateway ZZZ.ZZZ.ZZZ.2
- laptop 1 with mac os:
- this limitation comes from the ipsec "main mode" function and the "my_identifier" is address based
2015-07-02 12:31:18: ERROR: Expecting IP address type in main mode, but User_FQDN.
- IKE main mode with PSK allow id type = IP address only.
-
MacOS
-
FreeBSD
-
Linux
-
Windows
- PowerShell
- Github on Windows (optional)
easy ipsec configuration
-
MacOS
- ipsec connection
- openvpn connection
- (partial support)
-
FreeBSD
- ipsec connection
-
Linux
- ipsec connection
- openvpn connection
- restrictive firewall rules
- (for ipsec only traffic)
| Protocol | v4 | v6 |
|---|---|---|
| INPUT | DROP | DROP |
| FORWARD | DROP | DROP |
| OUTPUT | DROP | DROP |
| icmp | ACCEPT | ---- |
| icmpv6 | ---- | ACCEPT |
| dhcp | ACCEPT | ---- |
| ssh* | ACCEPT | ACCEPT |
| cifs* | ACCEPT | ACCEPT |
| udp 500 | ACCEPT | ACCEPT |
| udp 4500 | ACCEPT | ACCEPT |
| esp | ACCEPT | ACCEPT |
| broadcast | DROP | ---- |
| multicast | DROP | DROP |
| openvpn** | ALL | ALL |
* allow only outgoing connections
** allow all openvpn traffic
-
set static/permanent arp entry for the ipsecgatewayip
- restart (local):
- minidlna service
- unbound service
- restart (local):
-
Windows
- ipsec connection but NOT works!
- (windows ipsec support is only up to dhgroup14)
- ipsec connection but NOT works!
- Mac OS X 10.8+
- FreeBSD 10+
- Linux / Debian 8+
- Windows 8+ / 10+ (Technical Preview)
# ./easy_ipsec.sh
- run as administrator (allow the untrusted powershell scripts)
Set-ExecutionPolicy Unrestricted
- run as administrator
PS C:\github\easy_ipsec> .\easy_ipsec_win.ps1
- github plitc easy_ipsec [VERSION: 01.05.2015]
- freebsd racoon server <-> linux strongswan client
- github plitc easy_ipsec strongswan openvpn [VERSION: 01.07.2015]
- freebsd racoon server <-> linux strongswan client (outside) and openvpn client (inside)
-
04.10.2015: MacOS X Tunnelblick add useless route for openvpn routing (without removal routing is broken!)
-
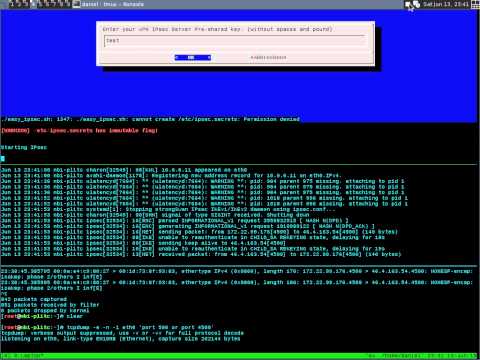
22.08.2015: FQDN policy resolving problems
ipsec[7812]: 08[IKE] IDir 'IP' does not match to 'FQDN'
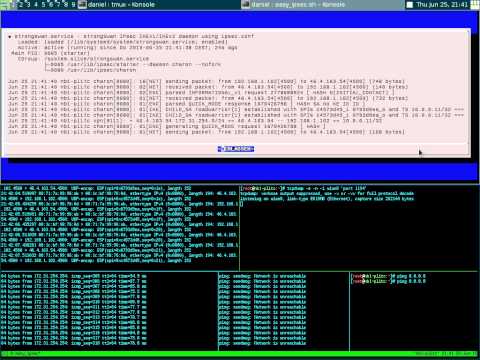
- 14.06.2015: interruption after ~1h 15 min
64 bytes from 172.31.254.254: icmp_seq=4931 ttl=64 time=18 ms
64 bytes from 172.31.254.254: icmp_seq=4945 ttl=64 time=16 ms
- 06.06.2015: NAT issues? (tcpdump)
NONESP-encap: isakmp: phase 1 I ident
NONESP-encap: isakmp: phase 1 R ident
NONESP-encap: isakmp: phase 1 I ident[E]
NONESP-encap: isakmp: phase 1 R ident[E]
NONESP-encap: isakmp: phase 1 ? oakley-quick[E]
NONESP-encap: isakmp: phase 2/others ? inf[E]
NONESP-encap: isakmp: phase 2/others ? oakley-quick[E]
- failed after delete system-logs (MacOS)