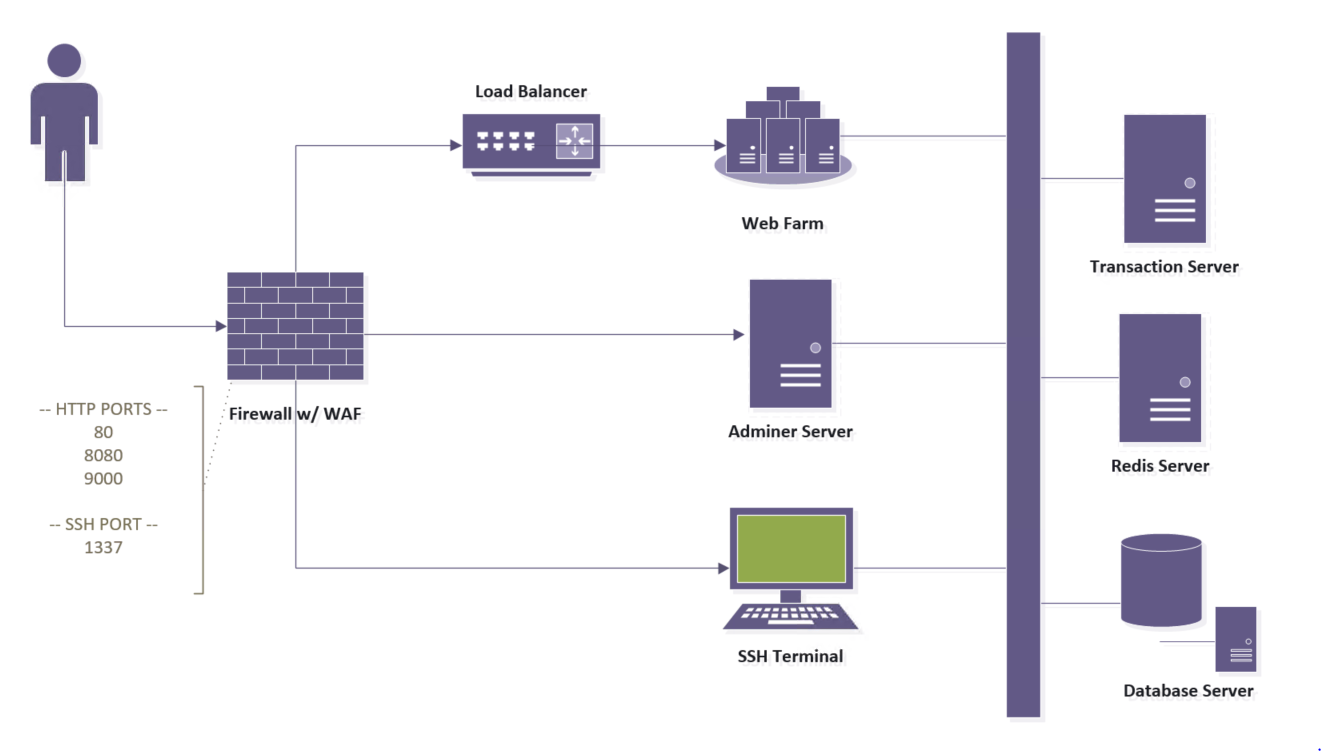
Exploitable App is a sandbox for exploring the various ways that applications can be exploited by attackers. Designed to emulate a banking application with various vulnerabilities the Exploitable App is a learning platform that attempts to teach about common web security flaws. The Exploitable App contains generic security flaws that apply to most web applications and it also contains vulnerabilities that specifically pertain to the .NET framework. The vulnerabilities in this app are intented to teach about application security and the code is commented in a way that will allow developers to follow along and learn how to avoid the most common vulnerabilities.
- Docker Desktop you must also Enable Kubernetes
- Helm v3
- Kubectl
- git
- Azure CLI if deploying into Azure
git clone https://github.com/postworthy/ExploitableApp.git
cd ExploitableApp/HelmCHarts
.\docker-desktop-install.ps1
git clone https://github.com/postworthy/ExploitableApp.git
cd ExploitableApp/HelmCHarts
.\docker-desktop-install.sh
git clone https://github.com/postworthy/ExploitableApp.git
cd ExploitableApp/HelmCHarts
.\aks-install.sh
Because the application is built using .NET Core you will want to start by getting the latest version of Visual Studio which is currently available for Windows and Mac. You will then need to install Docker for your system. Last but not least you will want to install Git for pulling the latest code from the repo.
After you have navigated to your working folder you will want to get the latest code for the project using git
git clone https://github.com/postworthy/ExploitableApp.git
Once you have cloned the repo open the ExploitableApp.sln file to start exploring the code.
If you are developing and distributing open source applications under the GPL License, then you are free to use this project under the GPL License. GPL FAQ
Contact me at [email protected] for more information on Commercial, Enterprise, and Government use of the this project.